Blocking WhatsApp on Windows 11 with AppLocker and Intune

Blocking WhatsApp on Windows 11 with AppLocker and Intune
Introduction
Last week I was having a chat with someone about WhatsApp and how dispite blocking the Microsoft Store App users were still getting the app downloaded and installed. I’ve not explored much of the Intune Endpoint Security configuration as I’ve been focusing on Autopilot and Application Deployments latley. So i decided i’d have a go over the weekend and here’s the steps I took to block it. This could be applied to any other app as well.
Why AppLocker?
Disabling the Microsoft Store alone isn’t enough—users can still install WhatsApp via web links. AppLocker provides a robust solution by blocking the app based on its package family name (PFN), ensuring installation and execution are denied.
It’s perfect for a deny of a single application, WDAC on the other hand is best for when you want to enforce an allow-list of trusted binaries, drivers and packaged apps.
Step-by-Step Guide
Step 1 — Identify WhatsApp Package Family Name
On a test device with WhatsApp installed, run the following PowerShell command:
Get-AppxPackage *WhatsApp* | Select Name, PackageFamilyName, PackageFullName | Format-List
this will output the exact package name and publisher you need for your AppLocker rule. WhatsApp’s PFN is typically:
5319275A.WhatsAppDesktop
Step 2 — Create an AppLocker Deny Rule
GUI Method (Recommended):
- Run
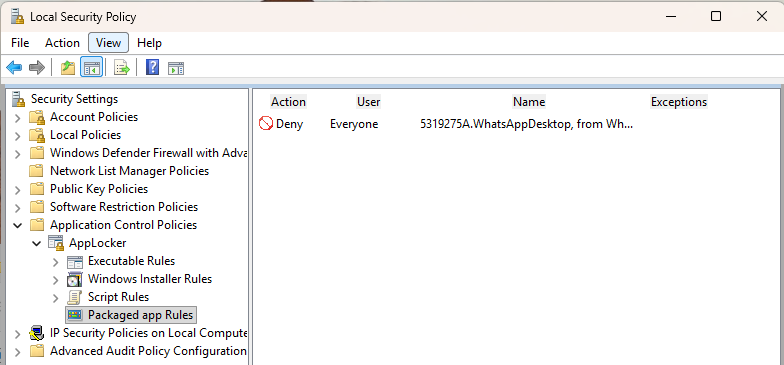
secpol.msc→ Application Control Policies → AppLocker → Packaged app Rules. - Right-click → Create New Rule → Action: Deny → User or group: Everyone (or a test group) → Next.
- Choose Use an installed packaged app as a reference, select WhatsApp from the list, and finish the wizard.
- In AppLocker properties, set Packaged app rules to Audit only for first-pass testing.
- I’ve also found from testing that you need to create the default policy as well which is an allow all wildcard. Without it, alot of things stop working like Notepad, Company Portal, New Outlook as they are all Appx based applications.
Step 3 — Export and Prepare the AppLocker Policy for Intune
- In the AppLocker MMC: right-click AppLocker → Export Policy → save as
AppLocker_WhatsApp.xml. - Open the exported XML, copy the
<RuleCollection Type="Appx" ...> ... </RuleCollection>block (keep the RuleCollection tags). - Save as UTF-8 text.
Example XML Block:
<AppLockerPolicy Version="1">
<RuleCollection Type="Appx" EnforcementMode="Enabled">
<FilePublisherRule Id="89c2ee41-7b31-4e2e-9637-35ca79b0e63d" Name="5319275A.WhatsAppDesktop, from WhatsApp Inc." Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="CN=24803D75-212C-471A-BC57-9EF86AB91435" ProductName="5319275A.WhatsAppDesktop" BinaryName="*">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="8be0f7bc-966d-41b3-98a5-5e95851e1750" Name="All signed packaged apps" Description="Allows members of the Everyone group to run packaged apps that are signed." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePublisherCondition PublisherName="*" ProductName="*" BinaryName="*">
<BinaryVersionRange LowSection="0.0.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>
<RuleCollection Type="Dll" EnforcementMode="NotConfigured" />
<RuleCollection Type="Exe" EnforcementMode="NotConfigured" />
<RuleCollection Type="Msi" EnforcementMode="NotConfigured" />
<RuleCollection Type="Script" EnforcementMode="NotConfigured" />
</AppLockerPolicy>
Step 4 — Deploy via Intune
- In Intune portal: Devices → Windows → Configuration profiles → Create profile.
- Platform: Windows 10 and later
- Profile type: Templates → Custom
- Add a setting:
- Name: AppLocker - StoreApps - Deny WhatsApp
- OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/{GUID}/StoreApps/Policy
(replace {GUID} with a randomly generated GUID) - Data type: String
- Value: Paste the
... XML block (ensure UTF-8 encoding)
- Assign to a small test device group. Save & create.
Step 5 — Force, Monitor, and Test
- Wait for device to receive the profile (or run Sync from Company Portal).
- Verify enforcement: AppLocker may require a restart.
- Check Event Viewer → Applications and Services Logs → Microsoft → Windows → AppLocker for events (IDs 8022/8024 for packaged app allowed/blocked).
The OMA-URI Value currently is set to Audit, with that inplace you will see logs being generated in Event Viewer > Applications and Services Logs > Microsoft > Applocker